Zoho ManageEngine
 IT RESOURCE MANAGEMENT SOLUTIONS
IT RESOURCE MANAGEMENT SOLUTIONS
- Manage identity and access
Manage, manage, and secure digital identities and privileged access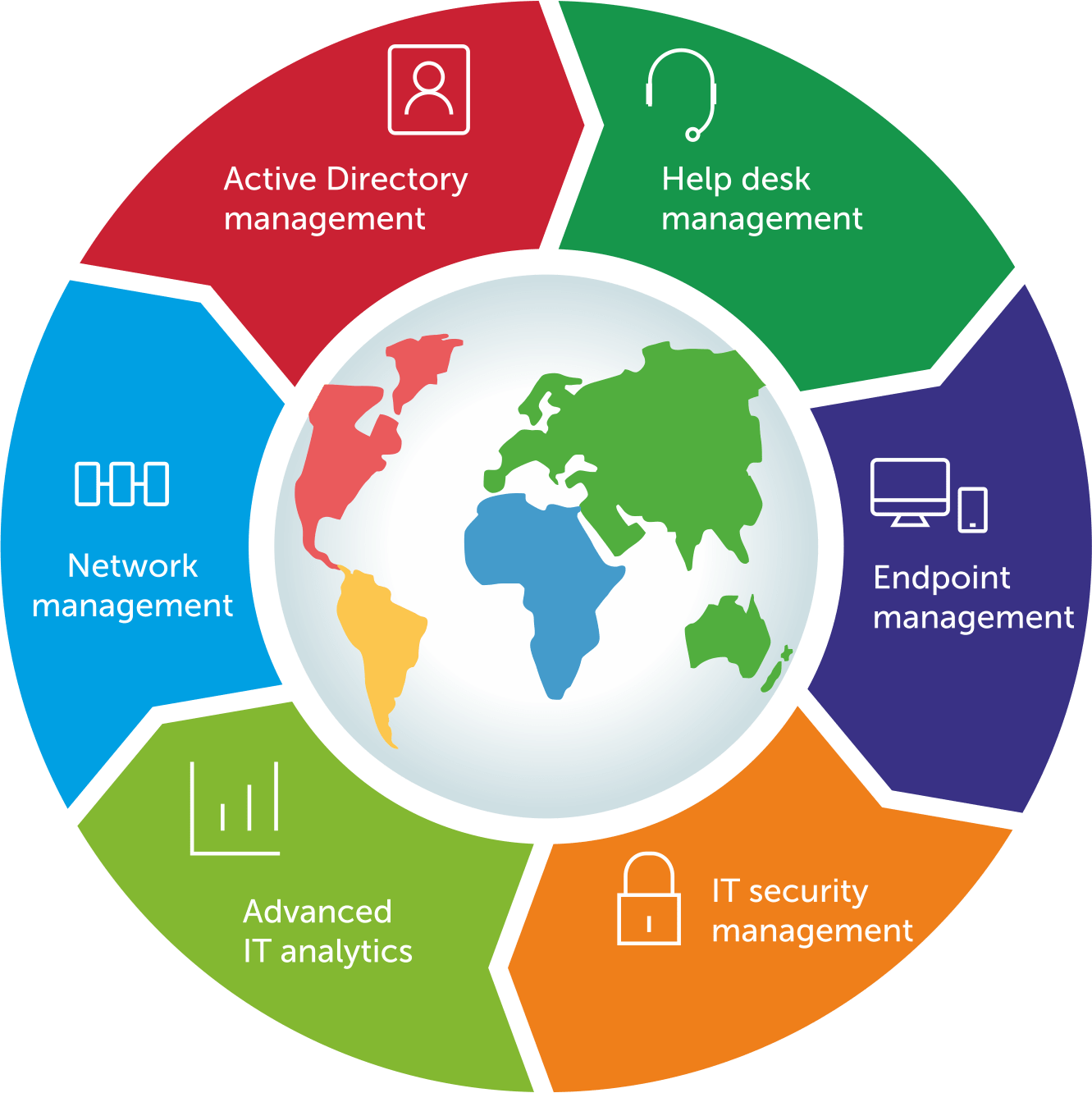
- Enterprise service management
Design, automate, deliver, and manage IT and business services - End-to-end endpoint management and security
Manage and secure desktops, servers, laptops, mobile devices, and web browsers - Manage IT operations
Monitor and manage your network, servers, and applications - Manage security-related information and events
Protect your network from cyberattacks and stay compliant - Advanced IT analytics
Manage identity and access
Identity and access management (IAM) solutions help to securely manage digital user credentials. IAM includes three main components: identification, authentication, and authorization. Restricting access to business-critical resources and protecting data helps IT administrators monitor for abuse of privileged access. IAM solutions protect your organization from security breaches by configuring system settings to detect anomalous activity that otherwise goes undetected. These IAM security features help you build an effective security infrastructure
Manage user credentials and access, deploy adaptive multi-factor authentication, protect privileged accounts with user behavior analytics, and ensure compliance for hybrid environments with Active Directory, Azure AD, Exchange, Microsoft 365, and more.
Manage the Active Directory service
- ADManager Plus – Manage and report on Active Directory, Microsoft 365, and Exchange services
- ADAudit Plus – Real-time audit changes for Active Directory, Windows files and servers
- ADSelfService Plus – Self-service passwords, endpoint multifactor authentication (MFA), conditional access, and enterprise single sign-on (SSO)
- Exchange Reporter Plus – Reporting, auditing, and monitoring for Exchange and hybrid Skype
- RecoveryManager Plus – Backup and recovery for Active Directory, Microsoft 365, and Exchange
Identity management and administration. Organize user identity management and access control for a zero-trust model.
- AD360 – Employee Identity and Access Management for Hybrid Ecosystems (Packaged Solution)
- M365 Manager Plus – Management, reporting, and auditing for Microsoft 365
- Identity Manager Plus – secure single sign-on for enterprise applications
Privileged access management. Control and provide privileged access to critical company systems.
- PAM360 – Complete privileged access protection for enterprises (packaged solution)
- Password Manager Pro – Privileged password management
- Access Manager Plus – Manage secure remote access and privileged sessions
- Key Manager Plus – Manage SSH keys and SSL/TLS certificates
Managing corporate services
- Establish and maintain customer relationships with seamless service management processes across the organization and contextual integration with enterprise applications.
- Increase employee productivity with a customizable self-service portal and a comprehensive service catalog.
- Get a quick, visual overview of all your requests and track them centrally with a Kanban-based ticket management system.
- Standardize service delivery with visual workflows and AI-powered automation.
- Get a single source of reliable data about your organization’s IT infrastructure with asset management.
- Create unique support plans and apply service level agreements to each service agreement.
Management of corporate and IT services. Ensuring the coherence of the work of employees from different functional units of the company.
- ServiceDesk Plus – End-to-end management of corporate services (packaged solution)
Customer service management. Create a centralized customer portal with efficient account management.
- SupportCenter Plus – customer support with built-in business accounts
IT asset management. Centralize and automate the full life cycle of IT assets.
- AssetExplorer – IT asset management with built-in configuration management database (CMDB)
End-to-end endpoint management and security (UEMS)
UEMS provides a comprehensive integration of device management and endpoint security. This increases employee productivity without compromising data security.
All entry points to corporate networks are constantly monitored for attacks. Often, it only takes one unauthorized device, uncontrolled browser, malicious application, or configuration error to shut down an entire network. It is impossible to manually track all these loopholes in the ever-growing number of endpoints that make up your network, so a UEMS solution comes to the rescue.
Endpoint management. Automate OS deployments, patching, mobile device management, and other day-to-day asset management tasks.
- Endpoint Central (formerly Desktop Central) – comprehensive endpoint management and security (packaged solution)
- Mobile Device Manager Plus – comprehensive mobile device management
- Patch Manager Plus – Automated patch management with support for multiple operating systems
- Patch Connect Plus – Automated patching of third-party software
- OS Deployer – Create and deploy OS images
- Remote Access Plus – Corporate remote access
Endpoint security. Proactively protect all endpoints and browsers from cyberattacks.
- Vulnerability Manager Plus – Manage company vulnerabilities with a focus on prioritization
- Device Control Plus – prevent data loss for peripherals
- Application Control Plus – Software detection and endpoint privilege management
- Browser Security Plus – Browser security and management
- Endpoint DLP Plus – Advanced endpoint data loss prevention
IT operations management
- Get a complete overview of the availability and performance of your network, virtual or physical servers, and disks.
- Monitor the performance of cloud applications, containers, databases, enterprise resource planning systems, large data warehouses, and applications and web servers.
- Perform end-to-end application monitoring with code-level diagnostics for Java, .NET, Ruby on Rails, Node.js, .NET Core, and PHP applications.
- Gain real-time visibility into bandwidth usage, analyze traffic consumption, and plan for future bandwidth needs accordingly.
- Analyze VPN activity and utilization, identify high traffic consumption, track target URLs, and block unwanted traffic.
- Block malicious traffic and monitor inbound and outbound traffic by scrutinizing traffic patterns over a period of time.
- Manage network configuration changes and backups to prevent network outages and reduce device downtime.
- Manage switch IP addresses and ports, detect and block rogue devices, and troubleshoot all network devices.
- Manage firewall rules, logs, policies, and configurations to harden your network and prevent network attacks.
Monitor network and server performance. Manage and optimize network, server, and application performance.
- OpManager Plus – Comprehensive network, server and application management (bundled solution)
- OpManager – Network performance monitoring
- NetFlow Analyzer – Bandwidth monitoring and traffic analysis
- Network Configuration Manager – network changes and configuration management
- Firewall Analyzer – Manage firewall rules, configuration, and logs
- OpUtils – Manage switch IP addresses and ports
Monitor application performance. Monitor, manage, and troubleshoot application performance.
- Applications Manager – Server and application performance monitoring
- Site24x7 – Comprehensive monitoring for IT administrators, DevOps and SREs
IT incident management. Receive instant alerts for critical incidents and provide real-time status updates.
- Site24x7 StatusIQ – Status pages for real-time status and incident notifications
Security information and event management (SIEM)
A SIEM solution protects your corporate network from cyberattacks and insider threats. It collects and analyzes security data generated by your devices in real time, alerting you to vulnerabilities, hacking signs, and any suspicious activity in a timely manner.
SIEM – to detect, investigate, and neutralize security threats.
- Log360 – Integrated SIEM with advanced threat analysis and machine learning-based user and object behavior analysis (UEBA)
Manage logs and compliance. Provide a more granular view of security event and compliance data.
- EventLog Analyzer – Comprehensive logging and compliance management for IT
- Firewall Analyzer – Manage firewall rules, configuration, and logs
Security audit. Audit Active Directory, cloud platforms, and files to improve security.
- ADAudit Plus – Real-time audit changes for Active Directory, Windows files and servers
- SharePoint Manager Plus – SharePoint reporting and auditing
- M365 Security Plus – Microsoft 365 Security
- Cloud Security Plus – Cloud security monitoring and analytics
- DataSecurity Plus – File auditing, data leakage prevention, and data risk assessment
- FileAnalysis – Analysis of file security and storage
Solutions for IT analytics
Today’s IT professionals don’t need standard analytics, they need a specialized solution that can extract valuable insights from disparate IT resource data. They need an analytics solution that combines machine learning and artificial intelligence technologies to identify patterns in IT data and apply them to existing problems. They need predictive information – not only for proactive infrastructure maintenance, but also for anticipating opportunities and proactively anticipating problems.
IT analytics. Connect to IT applications and visualize all aspects of your IT infrastructure.
- Analytics Plus – IT analytics based on artificial intelligence for enterprises