Acunetix

Acunetix Web Vulnerability Scanner is a standalone web vulnerability scanner
Acunetix Web Vulnerability Scanner automates the task of monitoring the security of Web applications and allows you to identify vulnerabilities in the protection of a Web site before they are detected and used by an attacker. It allows you to search for errors in scripts in PHP, ASP, ASP.NET and JavaScript.
Website tests can be carried out not only directly, but also through an HTTP or SOCKS proxy server – to ensure anonymity. Also performs HTTP authentication testing to identify insecure tinctures and weak passwords and to verify server security settings.
How Acunetix Web Vulnerability Scanner works:
- Acunetix WVS examines and forms the structure of the site, processing all the links found and collecting information about all detected files;
- The program then tests all web pages with elements for data entry, simulating data entry using all possible combinations and analyzing the results obtained;
- Upon discovering the vulnerability, Acunetix WVS issues an alert that describes the vulnerability and provides guidance on how to fix it;
- The resulting WVS report can be written to a file for further analysis and comparison with the results of previous checks.
What vulnerabilities Acunetix Web Vulnerability Scanner detects: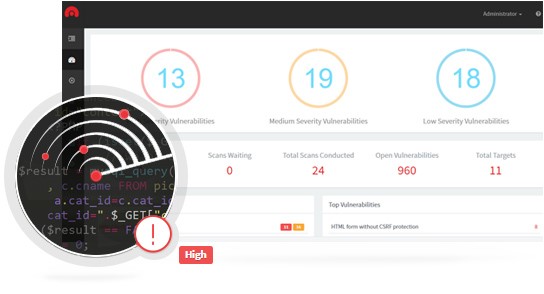
- Cross site scripting (execution of malicious script in the user’s browser when accessing and in the context of the security of a trusted site);
- SQL injection (executing SQL queries from the browser to gain unauthorized access to data);
- GHDB (Google hacking database) is a list of typical queries used by hackers to gain unauthorized access to web applications and websites.
To execute the code:
- Crawl the directory;
- File inclusion;
- Disclosure of the source code of the script;
- CRLF injection
- Cross frame scripting;
- Public backups of files and folders;
- Files and folders containing important information;
- Files that may contain information necessary to carry out attacks (system logs, application trace logs, etc.);
- Files that contain folder lists;
- A low-security folder that allows you to create, modify, or delete files.
Where to buy? For purchase inquiries feel free to contact us