Deceptive Bytes
Cybersecurity that quickly prevents any threats, regardless of their scale, is a guarantee of protecting your business.
We are a new generation of solutions for YOU
|
|
Active Endpoint Cyber DefenseIntelligent Threat Protection
|
A million new malware is created daily for espionage, theft, ransom and more, causing billions of dollars in damage.
CISO IT managers today are overloaded with work on the implementation of expensive endpoint protection products, forced to respond to any warning and false positive. In the event of a shortage of personnel, they are not able to cope with every such warning and are constantly in a stressful state, trying to eliminate the consequences of attacks.
To protect data, information security experts recommend that organizations use the new Deceptive Bytes technology
The solution is effective in preventing attacks:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
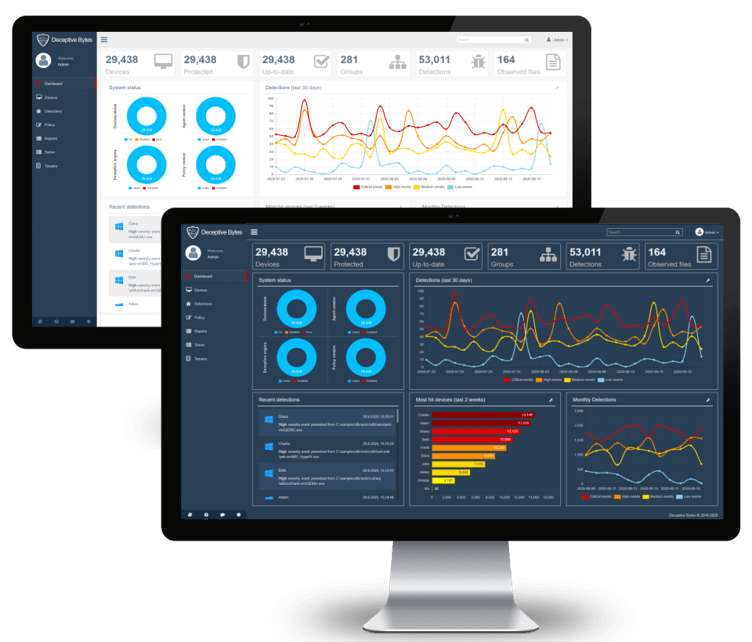
 Deceptive Bytes Active Endpoint Deception recognizes the targets of the attack, analyzes and makes decisions to protect objects, using their own methods for protection to block their actions, and thus disrupting the attack on the organization. An innovative solution that creates a dynamic false environment for any dangerous interference with the operation of protected objects, deters malware from fulfilling its malicious intentions.
Deceptive Bytes Active Endpoint Deception recognizes the targets of the attack, analyzes and makes decisions to protect objects, using their own methods for protection to block their actions, and thus disrupting the attack on the organization. An innovative solution that creates a dynamic false environment for any dangerous interference with the operation of protected objects, deters malware from fulfilling its malicious intentions.
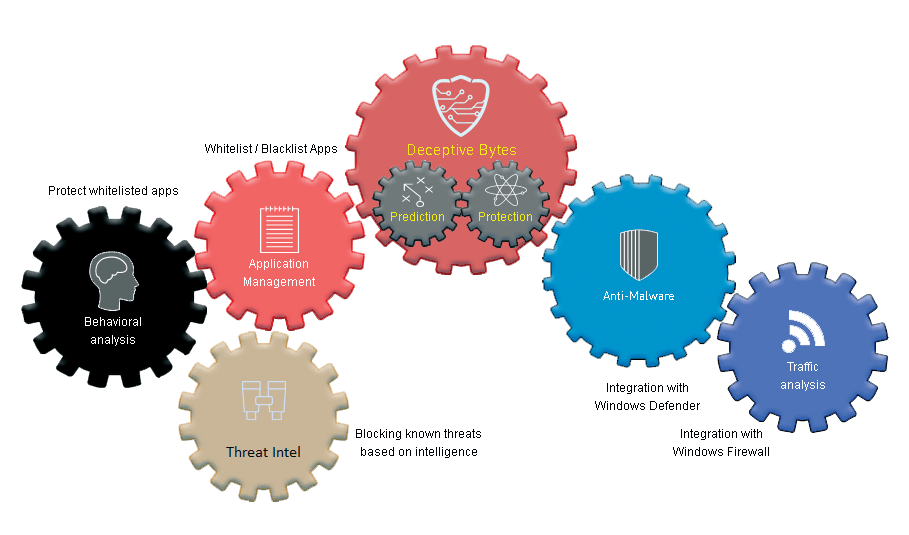
Deceptive Bytes – protection technologies
Deceptive Bytes End Point Protection is a high protection efficiency, more than 98%, which is achieved thanks to the technologies on which the software is built:
Preemptive Defense |
Proactive Defense |
| a way to predict possible attacks by searching for the “weak links” of the IT structure to protect them from possible infection. Create a dummy virtual environment to fool intruders | dynamic methods of responding to threats during an attack, predicting the targets of the attack at each stage and a flexible response – deceiving attackers who believe that they have succeeded |
At the heart of the method:
- Attack Deception: Creating a False Virtual Environment to Deceive Malware
- Behavioral analysis: monitoring user actions and protecting “legitimate” software from attack
- Application Management: Manages software based on company policies
- Antivirus software: Seamless integration with Windows Defender or other antivirus software
- Firewall: Manages the configuration of the Windows Firewall on the endpoint
- Information Gathering: Blocks known threats with web-based information
Evolution of protection technologies
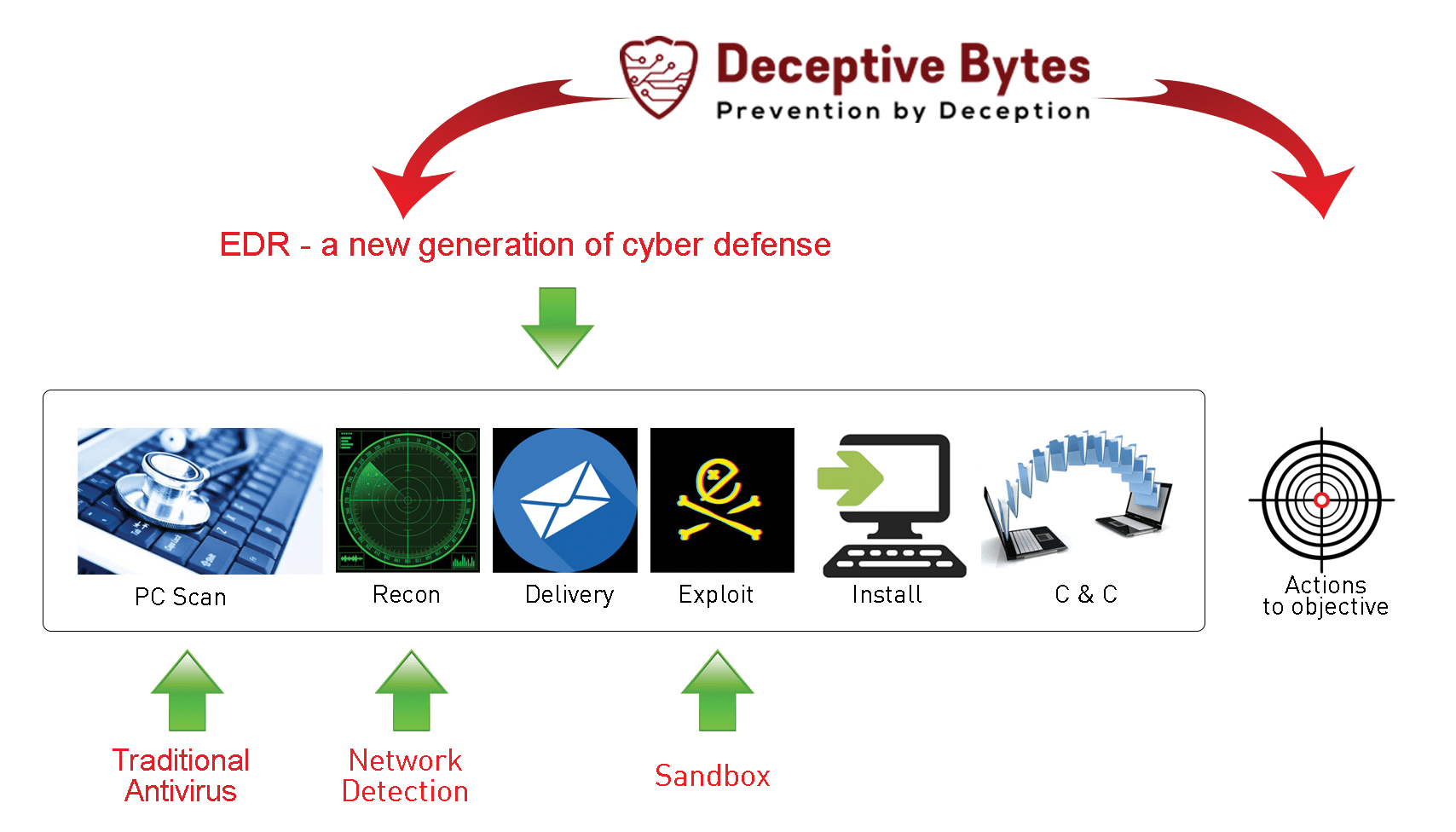
The Deceptive Bytes End Point Protection solution is an evolutionary development of existing technologies and includes their functionality without their drawbacks.
Comparison of Deceptive Bytes and other solutions when detecting a threat:
Disadvantages of existing solutions:
UBA / UEBA (behavioral analysis) – systems are sharpened to identify abnormal behavior, and the response to these cases is entrusted to the shoulders of the information security analyst;
EDRs (discovery and response) are focused on working with the OS of end devices, so in them, if any, general analytics are present, then in an extremely limited amount; EPP detection is triggered when the malware achieves partial or complete success and the victim is compromised before the attack is blocked;
SIEM systems (event collection and processing) in a large corporate network issue thousands of notifications, especially if correlation rules are enabled, so that SOC analysts are simply littered with these alerts and can miss something really important;
SOAR (orchestration, analysis, and response) encompasses most of the infrastructure components, but is focused on reactive actions in response to threats; there are usually no proactive opportunities in SOAR.
Network Deception – derived from the well-known Honeypot technology – create decoys and traps throughout an organization’s network to lure attackers to controlled servers where the attacker must be caught. Ineffective in attacking ransomware, crypto miners and fileless malware and “sideways movement” as these types of attacks have no visibility and control within the endpoint and can bypass traps.
Full integration with Windows Defender and Windows Firewall, as well as with other IT infrastructure protection solutions
This integration creates a comprehensive ecosystem that cross-links the signs of any attack and synchronizes incident remediation, creating additional layers of security to protect endpoints.
The Deceptive Bytes platform manages defender and firewall, on the one hand, and receives threat notifications on the other, giving a complete picture of the situation and promptly protecting the system.
And, although the solution incorporates the integration of the Deceptive Bytes platform with many well-known means of protecting the IT infrastructure from attacks, integration with the built-in “endpoint” protection tools can significantly reduce the cost of ownership of the entire complex ecosystem as a whole, while showing high efficiency with the optimal price-quality ratio.
Advantages of the solution for
Organizations
- Protection against unknown and advanced threats
- Prevent data and asset corruption
- Reduced reputational risk
- Reduced operating costs
CISOs/IT managers
- Automation of response time to detected malware
- Reduce alerts and false positives
- Adapt to changes in IT environments
- Use built-in security tools
- Use in any vulnerable environments and legacy systems
MSSP/Integrators
- Enhancing cybersecurity
- Protect multiple clients with 1 server
- Rapidly change the tactics of protection against new threats
- Additional protection against internal risks of security breaches
And the user gets…
- Increase employee productivity
- Reduced operating costs
- Protecting Remote Workers
- Achieve high ROI
Deceptive Bytes End Point Protection — is:
Proactive & Proactive Protection
- Prevents unknown and complex threats – prevent threats without the use of signatures and templates, based on the analysis of malware actions and finding ways to circumvent them
- High detection and protection rates – more than 98% efficiency in detecting, analyzing activity and evading threats, which helps to really protect the infrastructure
- Minimum detection and response time – Detect malware in real time and prevent it from evading protections. Quick response
Easy to use
- Comprehensive protection – does not require a full system scan, any unknown processes are processed
- Deploy in seconds – Installing the client (<15 MB) takes seconds. Starting up does not require a system reboot
- Easy to use – the solution runs and works autonomously, does not require intervention or additional configuration
- Extremely low resource usage (CPU, memory, disk) – the solution does not affect the health of systems, uses <0.01% of CPU resources, <20 MB of RAM and <15MB of disk space
No signatures
- No permanent updates – there is no need for constant updates, because the solution analyzes the general behavior of malware
- Works in standby mode – no constant updates allow you to work offline and remotely
- Stops millions of threats with just one evasion technique – the integration of just one evasion method protects against millions of threats that arise now or in the future
Flexibility
- High stability of work – the agent operates in the user mode, can not cause a system crash, or become an entry point to the system (full access only to the local OS)
- Automatic process list creation – analyze the system environment and create a whitelist of allowed local OS processes to control security
- Prevention of false alarms – the solution uses different methods of modeling the behavior of malware, which allows you to respond only to real threats
Where to buy? For purchase inquiries feel free to contact us