Portswigger
 Burp Suite is an integrated platform designed to audit a web application, both manually and automatically. Contains an intuitive interface with specially designed tabs to improve and speed up the attack process. The tool itself is a proxying mechanism that intercepts and processes all requests coming from the browser. It is possible to install a burp certificate to analyze https connections.
Burp Suite is an integrated platform designed to audit a web application, both manually and automatically. Contains an intuitive interface with specially designed tabs to improve and speed up the attack process. The tool itself is a proxying mechanism that intercepts and processes all requests coming from the browser. It is possible to install a burp certificate to analyze https connections.
Contains tools for mapping a web application, searching for files and folders, modifying queries, fuzzing, guessing passwords, and more. There is also a BApp store, which contains additional extensions that increase the functionality of the application.
This is the most popular set of utilities for testing web applications. If you look at the statistics and reports of bug-bounty programs – almost everywhere on the screenshots you can find the use of this tool.
The main functionality is based on the following modules:
- Proxy is an intercepting proxy server that operates over the HTTP(S) protocol in man-in-the-middle mode. Being between the browser and the web application, it will allow you to intercept, study and modify traffic going in both directions.
- Spider is a spider or crawler that allows you to automatically collect information about the architecture of a web application.
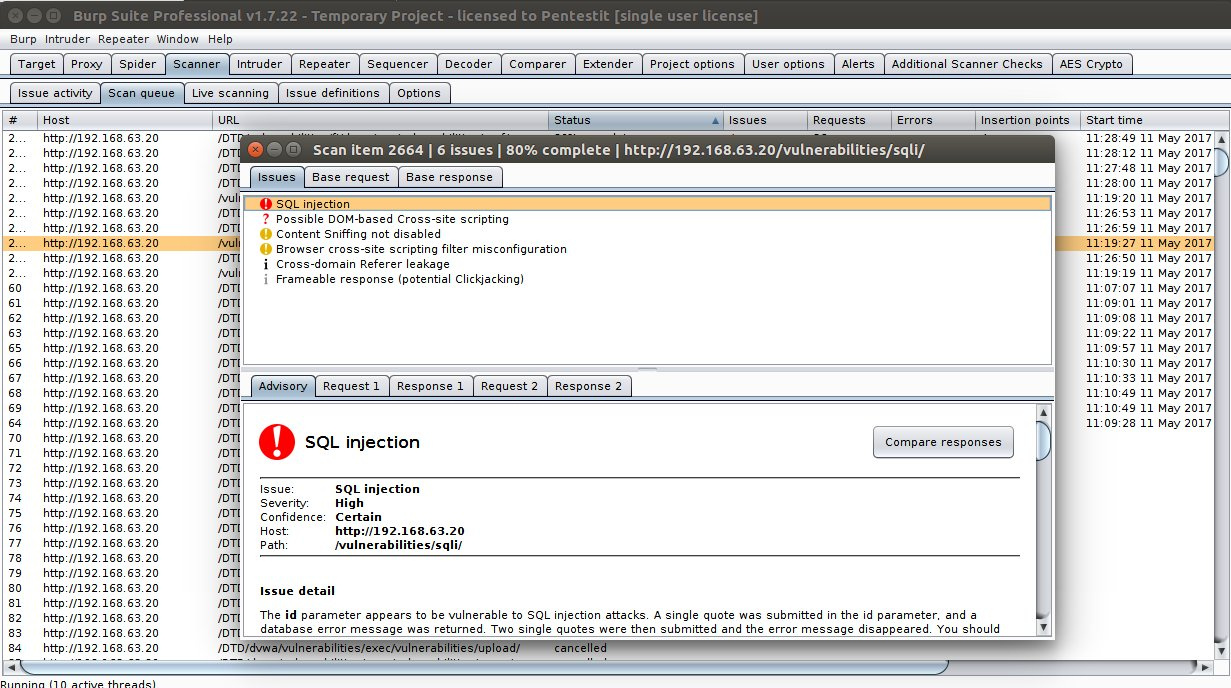
- Scanner — automatic vulnerability scanner (OWASP TOP 10, etc.) Available in the Professional version, in the free version only a description of the features.
- Intruder is a utility that allows you to automatically perform attacks of various kinds, such as password guessing, searching for identifiers, fuzzing, and so on.
- Repeater is a utility for modifying and resending individual HTTP requests and analyzing application responses.
- Sequencer is a utility for analyzing the generation of random application data, identifying the generation algorithm, predictive data.
- Decoder is a utility for manually or automatically converting web application data.
- Comparer is a utility for identifying differences in data.
- Extender is an extension in BurpSuite. You can add both ready-made from the BApp store, and your own development.
One of the main utilities for testing is Burp Intruder. How it works is that it processes each HTTP request (called a “basic request”), changing the parameters in various ways, issuing each modified version of the request, and analyzing the application’s responses to identify interesting features or behaviors of the web application.
Burp Intruder allows you to distinguish the following types of attacks:
- Sniper – a separate dataset is used – one field (the area marked with markers) – one payload. This type of attack is useful when individually testing fields for common vulnerabilities (such as XSS).
- Battering ram – this type of attack uses the principle – all fields – one payload. This can be useful when an attack requires putting the same data in multiple positions at once.
- Pitchfork – This type of attack uses multiple peylods for multiple fields. For example, on the first request, the first row from the first verification set will be placed in the first place indicated by markers. And the first line from the second set will fit on the second position. When the second query is generated, the second row from the first set will be placed in the first place, and the second row from the second set will be placed in the second set. This type of attack can be useful in situations where the application needs to send different, but somehow interconnected data all the time. For example, if you want to send a user’s name in one field and their ID in another.
- Сluster bomb – this type of attack uses a search of the main set of payloads and the addition of secondary ones. This is convenient to use, for example, to select passwords: at the first request, Intruder will place the first line from the first set of payloads on the first position, on the second first line from the second. For the second query, the first row of the first set will remain in the first place, and the second row of the second set will be placed on the second one. Then the third, and so on.
Where to buy? For purchase inquiries ask us